MacScan & Your Trojan Lesson
Despite the OS X platform being one of the most secure operating systems available, there are still hundreds of bugs just waiting to be exploited by some bored hacker. At the minute, we’re pretty safe from these sort of things, but it’s when you lower your guard that you get hit hard.
I know of a few anti-virus programs available for OS X, but they all come at a cost. With so little risks out there, many Mac users don’t see the need to spend money on a product that they probably won’t be needing a few years yet, but that might be dangerous complacency.
MacScan
Okay, so what exactly does it do? MacScan searches your entire Macintosh system for spyware, Trojans, and keystroke loggers. Once it finds them it lets you know and then safely removes them from your system. It also has the ability to locate administrative programs that could be used maliciously or inadvertently installed on your machine. It’s not free, but it is cheap and certainly worth a buy if you want to keep your system safe along with OS X’s built in Firewall.
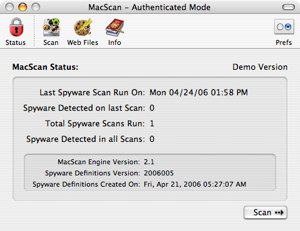
The main MacScan window
There are two key features of MacScan—One is the Scan itself, which locates the programs I’ve listed above, and the second is the cleaning of ‘Web Files’ area. I’m particularly keen on the Web Files section because it allows you to clean the cache of certain web-browsers, including Cookies, History, Downloaded Files List and Temporary Cache. Okay, so the cleaning process of all of those is pretty simple and easily done via the web browsers themselves, but MacScan makes the whole process even easier, allowing you to clean multiple browsers in one hit. The two main browsers used by us Mac addicts, Safari and Firefox, are both available in this list, but the very unpopular and poor Internet Explorer is also present. I’m unsure why they included this in the program as Internet Explorer is no more on OS X.
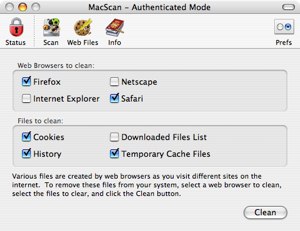
The Web Files window
The Scan feature is where it all kicks off though. You have three options available which all perform similar tasks. The ‘QuickScan’ scans only the current users home folder for trojan, spyware etc. The ‘FullScan’ feature, which is the one I recommend using, scans the entire hard-drive and is even more effective in authorized mode, which you are asked to activate upon opening the program using your systems username and password. The last feature, which isn’t available in the demo version, is the ‘CustomScan’. This is ideal if you only want to scan certain areas of the hard-drive, including CD’s, DVD’s and any memory sticks you have.
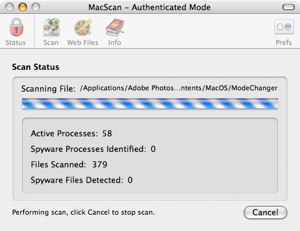
A scan in progress
Overall the program isn’t very advanced, but it does do an effective job and is relatively cheap, although I do think $24 (£14) is a tad much. However, if you wish to give it a try, you can download here for a free 15 day demo with only one, as far as I can see, feature blocked.
What’s a Trojan?
I’ve had criticism in the past (which I accepted) from many after not classifying the recent Mac OS X ‘virus’ outbreak correctly. Just to clarify for the new guys again, it wasn’t exactly an outbreak as only two were found and they weren’t actually virus’, they were trojan. So what’s the difference?
A trojan is a malicious program which enters the system in a disguise. Anyone who took History class at school knows that in the Greek story of the Trojan War, the Greeks gave a giant wooden horse to their foes, the Trojans, as an apparent ‘peace offering’. The Trojans dragged the horse inside their city before Greek soldiers would sneak out and open the city gates to allow their compatriots in. A Trojan Horse in PC terms works in much the same way.
A malicious program sits inside what appears to be a harmless file, either a picture, song, movie - anything really. Once the user opens that ‘harmless’ file, the nasty program inside pops out and wreaks havoc on your system. Now a Trojan isn’t the same as a virus as it does not replicate itself like a Virus does. It can, however, prove to be just as destructive.
What’s Spyware?
In its basic form, Spyware is installed on a users systems without the knowledge of the owner, you. It’s similar to a trojan in that it hides itself within a program, tempts a user to open and then runs a marathon within your system. The most appealing yet most annoying that I know of on the Windows platform is Bonzi Buddy, which is a cute monkey that apparently ‘helps’ the user in their Internet activities. Once you have Spyware on your system, it transmits data, normally for marketing or advertising reasons, back to the company who run the program. It picks up users activity and lets the guys back at base pick up information on you. In it’s worse form, Spyware can pick up credit card numbers, username, passwords and any other private information that you may have.
What about Keyloggers?
KeyLoggers are once again similar to Trojans and Spyware. They are used by some businesses to keep check on their employees in that they are doing the work they are supposed to. Used in a malicious way, keyloggers record every keystroke a user makes and sends that information back to a specified receiver. They can record everything from instant messages, e-mails, web site URL’s and even this article I’ve written. Installed in a similar way to Trojans and Spyware, Keyloggers are ideal for stealing information such as passwords and other sensitive information from a user.
As you can see, there are threats available to everyone using a computer in the world. Thankfully, Linux and the OS X systems are both at a low risk, but as I’ve said before, if you lower your guard, you’ll get hit and the next time you’re hit, it may be hard.
Turn that firewall on, download MacScan and be vigilant.


Comments