Using SSH: Secure Tunnels for the Common Man: Part I
In honor of the release of Chris Seibold's Big Book of Apple Hacks, here is a variation on a hack that appears in the book. Enjoy!
Secure Shell or SSH is a network protocol that provides secure communication between two computers. If SSH is used correctly, no eavesdropping or tampering with your data is possible, unless you are under attack by an immortal miscreant with extraordinarily powerful computers.
SSH is available in many forms -- as proprietary, open source, and free software from a variety of organizations. The most popular implementation is OpenSSH and this is the one that is part of Mac OS X.
Typically, SSH is used to securely log in to remote machines in order to execute commands. You can also use this secure connection to transfer files, run GUI programs under X windows, and forward ports. It is this last feature that will enable us to create secure tunnels between computers.
Tunnels: What and Why?
The purpose of an SSH tunnel is to secure the "last mile" of your connection. There are many reasons to want this, but the most common are in situations where your connection is monitored, restricted, or not secure. For example, if you are at a coffee shop using your laptop over the provided unencrypted WiFi connection, there is a chance that someone is eavesdropping on your communication. In such a situation, you could create a tunnel to a home machine to check your email securely.
Also, many people have certain kinds of applications or sites blocked or monitored by their place of work (or by their country). Setting up an SSH tunnel to a machine outside your work (or country) network will allow you to keep your communication private and to use applications that may otherwise be blocked.
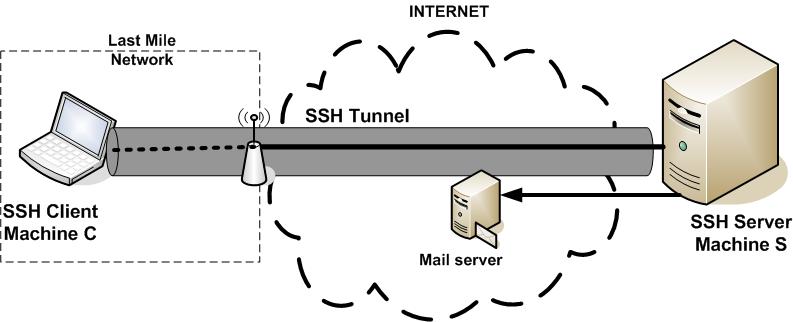
To set up an SSH tunnel, you require two computers -- one as the SSH client (machine C) and another as the SSH server (machine S). Machine C is insecure or restricted, while Machine S has full access to the Internet and is preferably under your control. In the example of an insecure wireless computer, Machine C is your wireless laptop and Machine S is a desktop connected to the Internet. In the example of securing your work communication, Machine C would be your work computer and Machine S could be a home computer connected to the Internet.
In order to set up an SSH tunnel, you will need the following:
- Two machines with SSH installed. Mac OS X comes with SSH, as do most variants of Unix and Linux. Windows users can try out Cygwin.
- At least one of which has "Remote Login" enabled (or SSH server configured for non-Mac machines). This can be done through the "Sharing" preference under "System Preferences."
- An Internet available Internet Protocol (IP) address for the server machine. Most broadband connections provide a unique IP for your home, though it may change frequently. You can find your global IP under the "Network" section of "System Preferences" if you are directly connected to your cable/DSL modem. If you are connected through a wireless router, you can find your IP in the administration interface for that device. An IP is a unique address for a machine that is accessible from anywhere on the Internet and is of the form w.x.y.z (where w, x, y and z are numbers between 0 and 255). You can also get a hostname for your IP address at services such as DynDNS.com.
You can prepare those resources, and in the next part of this article next week I will help you build the SSH tunnel.



Comments
This is a great inspiring article.I am pretty much pleased with your good work.You put really very helpful information. Keep it up. Keep blogging. Looking to reading your next post.
cheap chris brown tickets - cheap kelly rowland tickets